- What is Sidejacking ?

SideJacking works only if the site catches a non-SSL cookie, so any Web site that uses SSL exclusively would be safe from SideJackers. SideJacking was first demonstrated by Robert Graham, CEO of Errata Security at Black Hat in 2007.
- Techniques :
1. WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets bypassing the protocol stack, and has additional useful features, including kernel-level packet filtering, a network statistics engine and support for remote packet capture.
Download and install Winpcap from here.
2. Graham leveraged the tools Ferret, essentially a packet sniffing tool that captures cookies and writes them to a hamster.txt file, and Hamster, basically a local proxy that creates a web front end for exploiting the cookie information captured by Ferret.
Download and install Ferret & Hamster from here.
3. Unzip the tools into a directory such as C:\sidejacking.
4. Open a command prompt and change to that directory as cd c:\sidejacking.
5. Use ferret –W to figure out which interface you want to sniff.
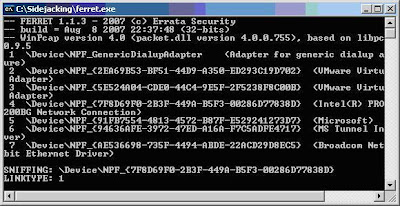
6. Use ferret –i n to start sniffing cookies. Here n is the interface number.
7. Now use hamster in the same directory as hamster.txt to start the proxy.

8. Set up a browser to use the proxy at 127.0.0.1:3128.
9. In that browser, go to http://hamster to go to the proxy console window.
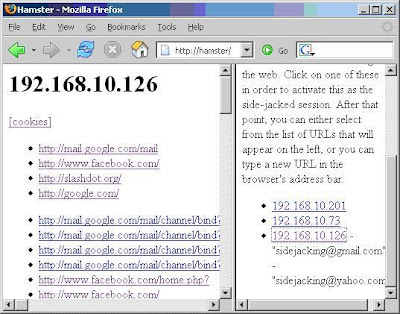
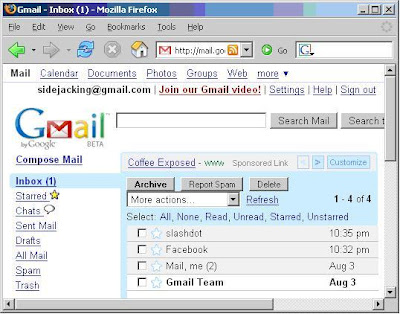
10. Select a victim, then click on a URL to sidejack it.
- Countermeasures :
2. Never use a Wi-Fi hotspot unless they are using VPN (virtual private networking) or SSL (secure sockets layer) to access sensitive information.
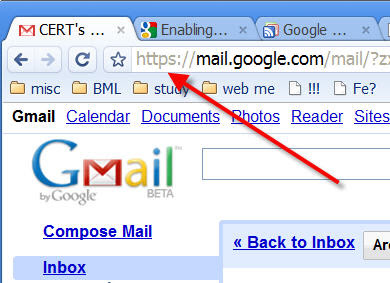
3. Graham said that Google Mail users could switch to https://mail.google.com and secure their session from such snooping.
Happy Hacking...Enjoy...
For educational purpose only...Do not misuse it...

it is fact that Sidejacking is dangerous for computer
ReplyDeleteHelp please i can't use cain, ferret with my wireless adapter. Help me out !
ReplyDeleteHi DaNi,
ReplyDeleteCheck this out: http://www.xtrmhack.com/2013/05/hack-facebook-by-session-hijacking.html
Thanks !